August 29, 2024

Remote OTA updates are evolving quickly, presenting opportunities for safety improvements alongside key questions about cybersecurity risks
According to research, up to 95% of cars are expected to have internet connectivity by 2030. Many drivers associate connected vehicles with conveniences like streaming music and maps, but this functionality is playing an increasing role in improving vehicle performance, reliability, safety, and overall user experience — without requiring visits to the dealership.
Over-the-air (OTA) software updates can quickly deliver improvements and modifications to virtually any Wi-Fi-enabled system. Chief among the key benefits of OTA updates is the potential to improve recall compliance for key safety features while reducing the time and cost of in-person service visits. However, although OTA updates are more likely to bolster cybersecurity defense by keeping software systems up to date, they do raise questions for OEMs and consumers — who can choose to opt in to or out of OTA updates — about access to interconnected vehicle systems, potential malware and related cyberattacks, and data privacy issues.
How OTA updates work
Over-the-air updates are essentially software system updates delivered to vehicles via cellular data or Wi-Fi networks, much like smartphone software and system updates. Most vehicle systems today are computerized and include a variety of related technologies. Examples of these systems include:
- Infotainment — music, maps, interior lighting, cell-phone integration, etc.
- Braking and stability control — anti-lock brakes (ABS), electronic stability control (ESC), adaptive suspension systems, etc.
- Advanced driver assistance systems (ADAS) — forward collision warning (FCW), automatic emergency braking (AEB), lane departure warning (LDW), blind-spot monitoring, adaptive cruise control (ACC), auto high-beam headlights, etc.
- Drivetrain management — engine control unit (ECU), engine throttle, fuel mixture, timing, turbocharging, exhaust, automatic transmission, all-wheel-drive control systems, etc.
- Electric vehicle systems — performance and electric motor control, energy management, battery state and health monitoring, etc.
Virtually every system in a modern vehicle is at least partially computer controlled and thus has the potential to be modified with OTA updates. While there will still be vehicle systems that require component updates to be done in person at a dealer or authorized service center, many safety-critical vehicle systems can be updated with OTA, and the number of manufacturers equipping their vehicle with OTA update capabilities is growing.
OTA updates for recalls — the case for improved safety
In 2017, the National Highway Traffic Safety Administration (NHTSA) published an extensive report on vehicle recall compliance titled "Vehicle Safety Recall Completion Rates Report." The report includes data about manufacturer safety and other recalls from 1986 to 2017. According to NHTSA, the recall completion rates for most vehicle component categories fall within a range of 60-75% (see fig. 1, representing a four-year sample of recall rates from within the broader report), many of which are now computer controlled and may be appropriate for future OTA software updates.
Recall Completion Rates by Component from NHTSA
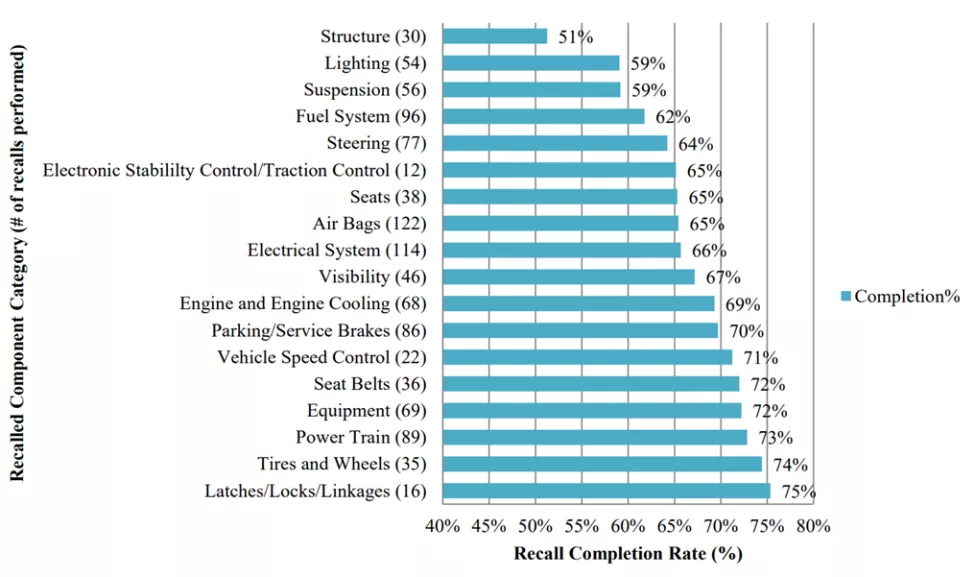
One key benefit of OTA updates is their potential to increase recall compliance rates for vehicle systems. Instead of asking customers to schedule time with a dealer for a software update, automakers can push updates to vehicles with the owners' permission. The use of OTA to address recalls is already happening, representing over 300 models across 23 brands as of 2023.
NHTSA has not issued compliance statistics for these OTA recalls, but rates will likely be higher thanks to the ease of deploying them. These recalls could also be lower in cost for OEMs when compared to software updates that require trained technicians and dealership visits. There's no guarantee, however, that OTA updates will reach 100% completion rates. Some cars may be out of range of wireless data connections, or their owners may opt out of receiving them.
Cybersecurity challenges for OTA updates
The nature of modern vehicles, accessible to OTA updates through Wi-Fi, creates inherent questions around whether those same pathways can be used to introduce harmful or dangerous features to a vehicle or to steal a driver's personal information. Research efforts to prove the risks associated with these vulnerabilities (e.g., "hacking for good") point to the continued need for vigilance among OEMs and advanced engineering capabilities that bring together expert knowledge of how integrated systems, sensors, and software work together.
In recognition of the cybersecurity risks associated with OTA security updates, NHTSA published a comprehensive report in 2020 that examined various malware attack vectors and how automakers can shield against them. The potential risks of installing malware through OTA updates can include:
- Intentional vehicular crash
- Disruption of operation (for example, loss of some or all controls while driving)
- Disruption of service (for example, the inability to use a parked vehicle)
- Coordinated attack (involving use of the prior attacks in coordination)
- Vehicle theft
- Vehicle parts or contents theft
- Intellectual property theft
- Private information theft — including credit card information
- Unauthorized activation of upgrade features (e.g., software piracy)
- Aftermarket performance tuning
NHTSA also identified several vectors for malware injection, including the possibility of hackers sneaking malware into vehicles at factories and parts suppliers, using software updates to spoof software servers, forging secure software signatures, or using stolen signing credentials.
Additionally, automotive software can be hacked via app store updates, if available, to infotainment systems. Denial of service (DoS) attacks prevent OTA updates from occurring or interrupt them in some way, which could disable vehicles for an indefinite amount of time or even irreversibly damage or "brick" computer processors and onboard equipment. Hackers can deploy DoS attacks by spoofing automobiles and sending false information to confuse the OTA server, posing as legitimate wireless access points, or jamming wireless communications altogether.
NHTSA highlights strategies for mitigating automotive software hacking. Some of these include:
- OpenVPN Implementation: Transport-layer security and OpenVPN are considered secure against most attacks. In this scenario, both the car and the network have a public and private key, creating a bi-directionally secure channel.
- Secure In-Vehicle Networks: Standard automotive controller area network (CAN) technology cannot support encryption. However, ethernet or CAN Flexible Data Rate systems can be encrypted and are difficult to hack.
- Entity Authentication: Currently automotive communication systems include strong security barriers between themselves and the outside world but little or no barriers within systems. Entity authentication creates additional layers of security within automotive systems, separating the critical functions of the vehicle from entertainment systems, for example.
- Software Version Rollback Protection: Prevents hackers from rolling software back to older, less secure versions.
These mitigation strategies can help automakers prevent malicious software from harming cars and their drivers, but OEMs will want to take care to ensure the updates they push are safe for their whole fleet. While OTA updates offer a potential solution for staying ahead of malicious threats through continuous security updates, they also introduce greater complexity by affecting all vehicles at once, instead of just the ones that come into the shop. Automotive manufacturers and system developers can use software testing, offensive and defensive models, and deployment methods refined by tech companies over the past several decades to vet their updates and help prevent unintended issues.
The future of OTA updates
Thus far, cybersecurity OTA update breaches have remained largely a theoretical threat. Modern vehicles are complex, well-protected systems that are not easily accessed. OEMs can use encryption keys that a vehicle's onboard system compares to its cryptographic keys, so that only software with matching keys can be installed, to verify software updates in-car. These encryption keys are extremely difficult to break and help vehicle systems confirm that software updates come from trusted sources.
OEMs also have opportunities to silo various car systems to ensure they can't be hacked from outside. For example, many automakers sequester the infotainment system from critical ADAS computers so OTA and other infotainment software updates can't interfere with the operation of the car. Some automakers deploy critical systems OTA updates by using advanced cryptography through proprietary networks. This is designed to prevent hackers from accessing vehicles remotely to install malware.
Security is paramount in modern automotive design, and automotive software and hardware engineers are adding more features and protections to prevent hackers from gaining access to critical systems. It is essential that the security measures necessary to protect vehicles and their drivers are integrated into software and hardware from the initial stages of the product lifecycle. For OEMs, manufacturing production serves as an acute phase in this process, with substantial downstream impacts to the overall cybersecurity of the vehicle.
Going forward, OTA updates have the potential to improve automobiles in the same way continuous software development has improved computing. In the future, more automakers are likely to roll out OTA updates of increasing importance to vehicle performance and safety, requiring continued diligence and advancements in software encryption and network solutions to minimize security risks.
What Can We Help You Solve?
Electrical and electronic systems in passenger and commercial vehicles are rapidly growing more complex as innovative new technologies are implemented. Exponent's electrical engineers and computer scientists have the industry experience necessary to increase the viability of your ADAS applications, from vehicle-level integration requirements to individual subsystem and component design validation.

Component, System, and Vehicle Analysis & Testing
Cutting-edge automotive research, product evaluations, and real-world vehicle testing.

Vehicle & Component Performance Analysis
Examine the strength, integrity, and performance of vehicles driven by internal combustion, and electrical and hybrid technologies.
Vehicle Engineering
Rigorous research on the safety and performance of all types of transport and cutting-edge technologies.
Emerging Vehicle Technology Development
Balance safety and performance while advancing innovative transportation technologies.
Electrical Engineering & Computer Science
Understand your most formidable performance, safety, security, and compliance challenges.

Vehicle Electronics & Electrical Systems
Increase the viability of your ADAS applications with optimal design and function.





